Status Dashboard
- This document contains unedited notes and has not been formally proofread.
- The information provided in this document is intended to provide a basic understanding of certain technologies.
- Please exercise caution when visiting or downloading from websites mentioned in this document and verify the safety of the website and software.
- Some websites and software may be flagged as malware by antivirus programs.
- The document is not intended to be a comprehensive guide and should not be relied upon as the sole source of information.
- The document is not a substitute for professional advice or expert analysis and should not be used as such.
- The document does not constitute an endorsement or recommendation of any particular technology, product, or service.
- The reader assumes all responsibility for their use of the information contained in this document and any consequences that may arise.
- The author disclaim any liability for any damages or losses that may result from the use of this document or the information contained therein.
- The author reserve the right to update or change the information contained in this document at any time without prior notice.
- Any attempts to perform penetration testing or ethical hacking on systems or networks should be done with the explicit permission of the system/network owner. Unauthorized access is illegal and can result in serious legal consequences.
- It is important to fully understand the scope of the testing and to only test within that scope. Testing outside the agreed upon scope is considered unauthorized and may result in legal action.
- Any findings or vulnerabilities discovered during testing should be reported to the system/network owner immediately and kept confidential until a fix can be implemented.
- It is recommended to use a separate, dedicated testing environment rather than testing on a live production system to minimize the risk of accidentally causing damage or downtime.
- It is important to take steps to protect your own identity and prevent accidental data leaks or exposure of sensitive information during testing.
- It is also recommended to follow a standard code of ethics for ethical hacking and penetration testing.
***********************************************************************************
Sample Dashboard
Creating a Sample Dashboard with Excel Pivot Tables and Graphs. Rationale for the Parameters Selected in the Dashboard. Different methods are available for creating dashboards, including Power BI and Tableau.
- Showcasing the overall - SLA or RAG [Red Amber, Green] status under two categories, to have a better holistic picture.
- Status - Done, next Status - Failed, Pending, canceled and Onhold
- Breaking down the status on which are - Critical, Important and Non-critical, throws light on Severity.
- Understanding the cost involved as per resource type.
- Getting info on Mean time to repair MTTR- per resource involved and number of tickets status as per resource group.
- The data sets are previewed through the statutory buckets, along with the calendar timeline and asset types involved.
- The various categories of Pindex were listed by status, then by quarterly and finally their importance to understand the severity.
 |
| Fig 01: Dashboard |
 |
| Fig 02: Dashboard: Part01 |
 |
| Fig 03: Dashboard: Part02 |
 |
| Fig 04: Dashboard: Part03 |
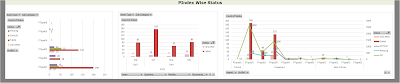 |
| Fig 05: Dashboard: Part04 |
POWER-BI Dashboard
Sample Data : Shop sales data
 |
| Powerbi-Shop-data-Dashboard-Page-01 |
 |
| Powerbi-Shop-data-Dashboard-Page-02 |
 |
| Powerbi-Shop-data-Dashboard-Page-03 |
 |
| Powerbi-Shop-data-Dashboard-Page-04 |
 |
| Powerbi-Shop-data-Dashboard-Page-05 |
 |
| Powerbi-Shop-data-Dashboard-Page-06 |
 |
| Powerbi-Shop-data-Dashboard-Page-07 |
 |
| Powerbi-Shop-data-Dashboard-Page-08 |
 |
| Powerbi-Shop-data-Dashboard-Page-09 |
 |
| Powerbi-Shop-data-Dashboard-Page-10 |
Steps involved in creating the dashboard:
01
 |
| Powerbi-Window |
03
 |
| Power Bi--Transform-First-row-as-headers |
04
 |
| Power Bi--Transform-Changing-Data-Type-and-Ignoring-any-errors |
05
 |
| Power Bi--Transform-Append-queries-as-new |
06
 |
| Power Bi--Transform-Append-queries-as-new_slect_two_tables |
07 |
| Power Bi--Transform-Inner-join-matching-rows |
08 |
| Power Bi--Transform-Append-queries-as-new_select-Columns-to-display |
09
 |
| Power Bi--Transform_Groupby_sum |
10
 |
| Power Bi--Transform_Groupby_advance |
11
 |
| Power Bi--Transform_Pivot-by-column |
12
 |
| Power Bi--Transform_UN-Pivot-by-column |
13 |
| Power Bi--Transform-View menu-profile-change to entire set |
14
 |
| Power Bi--Add-column-conditional-column |
15 |
| Power Bi-Shop-data-Transform-Home-Merge-queries-left outer-join |
16 |
| Power Bi-Shop-data-Transform-Home-Add-Col-Custom-col-formula |
17 |
| Power Bi-Shop-data-Transform-Home-Merge-queries-left outer-join-replace-null |
18
 |
| Power Bi-Shop-data-Transform-Home-Add-Col-Customc-col-formula-discount-values |
19
 |
| Power Bi-Shop-data-Transform-All-columns-calculated |
20 |
| Power Bi-Shop-data-ModelView-drag-a-common-column-to-other-Relationship-formed |
21 |
| Power Bi-Shop-data-ModelView--Relationship-created |
22 |
| Powerbi-Shop-data-chart-filter-on-visual |
23 |
| Power Bi-Shop-data-Report-View-Top-Bottom-5 |
24 |
| Powerbi-Shop-data-Report-View-Scatter-plot-Don't-summaries |
25
 |
| Power Bi-Shop-data-Report-View-Uncheck-Blank-Values-from-Filter |
26 |
| Power Bi-Shop-data-Report-View-Map-chart-select-city |
27 |
| Powerbi-Shop-data-Transform-Adding-Index-column |
28
 |
| Powerbi-Shop-data-Transform-Adding-Index-column-Move-to-beginning-change-data-type |
29 |
| Power Bi-Shop-data-Report-Create-new-table-create-new-measure |
30
 |
| Powerbi-Shop-data-Model-view-creating-relationship-active-and-inactive |
31
 |
| Powerbi-Shop-data-Report-View-two-date-filters-Edit-interactions |
32
 |
| Power Bi-DataFlow-step-02-On-premises data gateway-download-install |
33
 |
| Power Bi-Dataflow-step-03-Connecting-dataflow-from-web-to-On-premises |
Search keywords: Status Dashboard, GRC, governance, Risk, Compliance, gouti1454, quality management, cybersecurity, information security.























Comments
Post a Comment